Single Sign-On (SSO)
Overview
SSO is currently only available for Enterprise customers, and only Workspace admins can use this feature. To upgrade, get in touch with our sales team.
Single Sign-On (SSO) allows your team to log in to ElevenLabs by using your existing identity provider. This allows your team to use the same credentials they use for other services to log in to ElevenLabs.
Guide
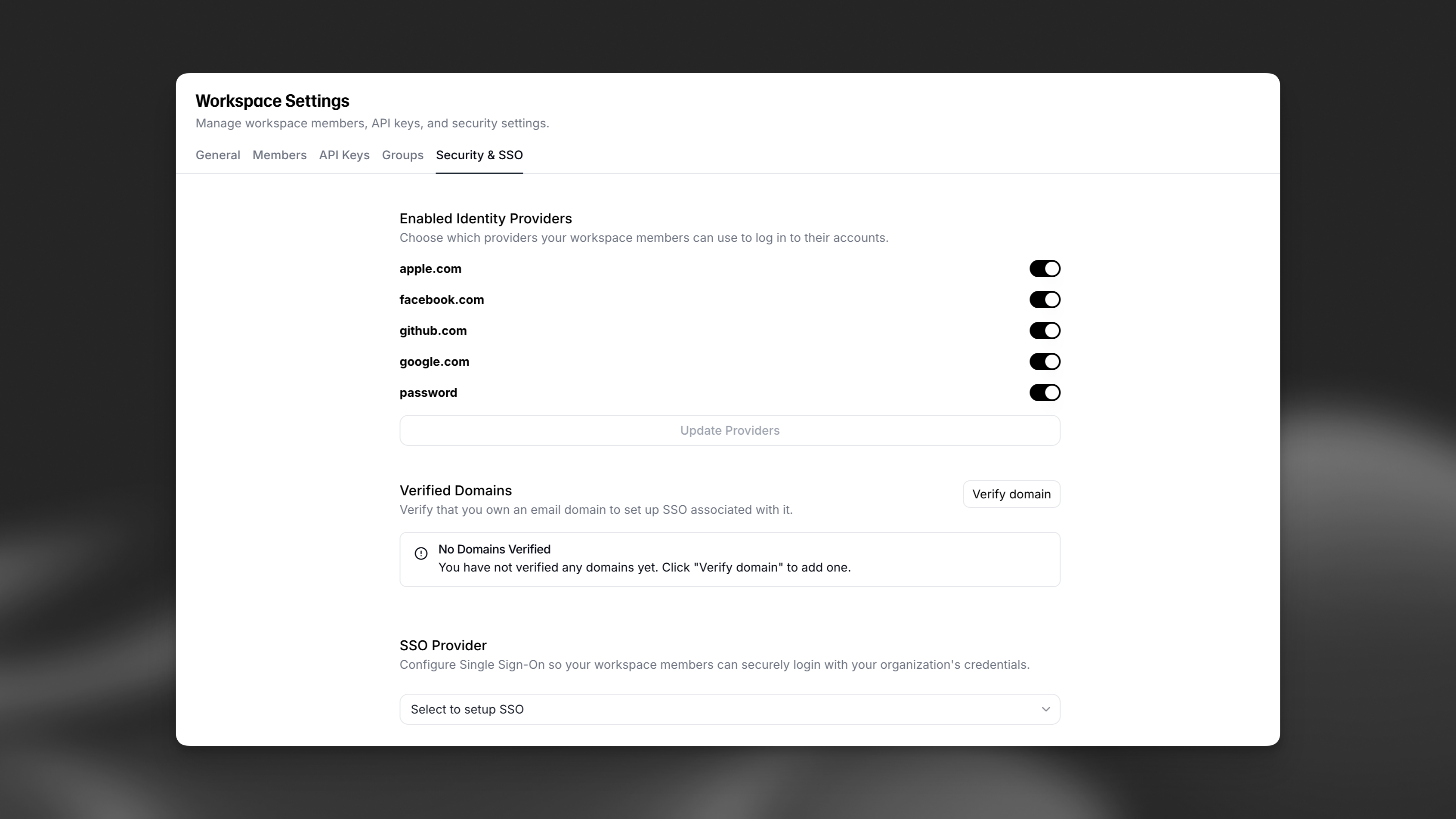
Access your SSO settings
Click on your profile icon located in the top right corner of the dashboard, select Workspace settings, and then navigate to the Security & SSO tab.
Choose identity providers
You can choose from a variety of pre-configured identity providers, including Google, Apple, GitHub, etc. Custom organization SSO providers will only appear in this list after they have been configured, as shown in the “SSO Provider” section.
Verify your email domain
Next, you need to verify your email domain for authentication. This lets ElevenLabs know that you own the domain you are configuring for SSO. This is a security measure to prevent unauthorized access to your Workspace.
Click the Verify domain button and enter the domain name you want to verify. After completing this step, click on the domain pending verification. You will be prompted to add a DNS TXT record to your domain’s DNS settings. Once the DNS record has been added, click on the Verify button.
Configure SSO
If you want to configure your own SSO provider, select the SSO provider dropdown to select between OIDC (OpenID Connect) and SAML (Security Assertion Markup Language).
Once you’ve filled out the required fields, click the Update SSO button to save your changes.
FAQ
Microsoft Entra Identifier / Azure AD - SAML
What to fill in on the Entra / Azure side:
- Identifier (Entity ID): Use the Service Provider Entity ID value from the ElevenLabs SSO configuration page.
- Reply URL (Assertion Consumer Service URL): Use
https://elevenlabs.io/__/auth/handler- For EU residency, use
https://eu.elevenlabs.io/__/auth/handler - For India residency, use
https://in.elevenlabs.io/__/auth/handler
- For EU residency, use
- ACS URL: Same as the Reply URL above.
What to fill in on the ElevenLabs side:
- IdP Entity ID: Use the Microsoft Entra Identifier (the full URL, e.g.,
https://sts.windows.net/{tenant-id}/) - IdP Sign-In URL: Use the Login URL from Entra / Azure
Okta - SAML
What to fill in on the Okta side:
- Audience Restriction: Use the Service Provider Entity ID from the ElevenLabs SSO configuration page.
- Single Sign-On URL/Recipient URL/Destination: Use
https://elevenlabs.io/__/auth/handler- For EU residency, use
https://eu.elevenlabs.io/__/auth/handler - For India residency, use
https://in.elevenlabs.io/__/auth/handler
- For EU residency, use
What to fill in on the ElevenLabs side:
- Create the application in Okta and then fill out these fields using the results
- Identity Provider Entity Id: Use the SAML Issuer ID
- Identity Provider Sign-In URL: Use the Sign On URL from Okta
- This can generally be found in the Metadata details within the Sign On tab of the Okta application
- It will end in /sso/saml
OneLogin - SAML
What to fill in on the OneLogin side:
- Recipient: Use
https://elevenlabs.io/__/auth/handler- For EU residency, use
https://eu.elevenlabs.io/__/auth/handler - For India residency, use
https://in.elevenlabs.io/__/auth/handler
- For EU residency, use
OIDC - Common Errors
Please ensure that email and email_verified are included in the custom attributes returned in the OIDC response. Without these, the following errors may be hit:
- No email address was received: Fixed by adding email to the response.
- Account exists with different credentials: Fixed by adding email_verified to the response
I am getting the error 'Unable to login with saml.workspace...'
- One known error: Inside the
<saml:Subject>field of the SAML response, make sure<saml:NameID>is set to the email address of the user.